 Seal the Secret !!
Seal the Secret !!
2022-Aug-18

By:DALEEP SINGH
2022-Feb-14 09:02:28
People talk about containers, use them to deploy their applications, part of complex architecture, serving many endpoints. And since, it allows us to connect these endpoints, networking these containers become equally important.
In our previous articles, we used Podman to create and run containers as root user, we were able to get IP address of the containers and also able to see the entire virtual components that help us to get the containers networked, which included bridge, VETH pairs, IPTables rules, etc. However, when we proceed to create a container as a regular user and look for the IP address of the containers, things start getting interesting, as we don't find any IP address on inspecting the container. The only solution to connect to rootless containers is host-based port mapping which allows you to connect to the container on the host IP address and the port exposed.
The question that remains is, how does rootless containers allow network access?
To provide network access to rootless containers, Podman takes help of slirp4netns, which provides user-mode networking ("slirp") for unprivileged network namespaces.
Let me first show what is done behind the scenes. We will start a process and put it in the network namespace and as expected, it will only have a loopback interface created. However, we cannot use loopback to communicate, hence, we need to create an interface and also assign some IP address to the same.

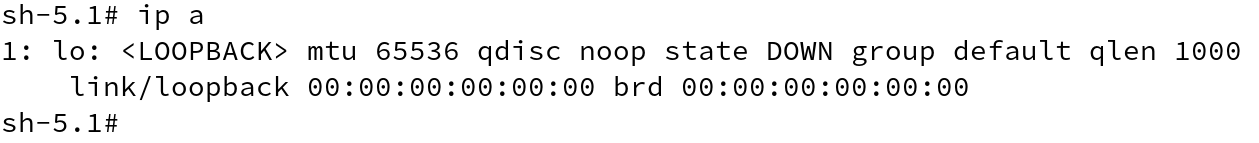
Using the command echo $$, we get the current PID of the process and using lsns -p , we can also get the namespace identifiers.

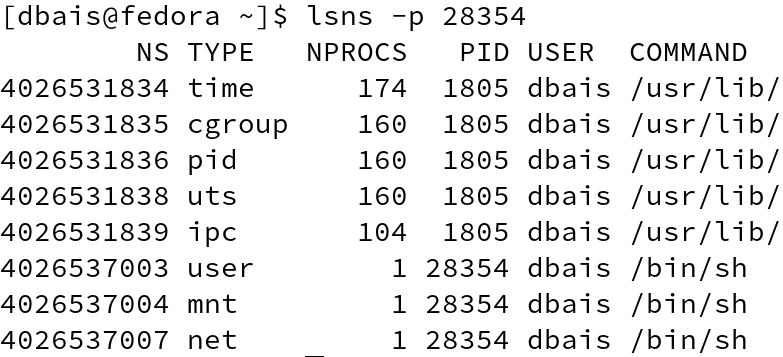
In this case, since, I am running as a non-privileged user, using the PID, on new terminal, let us use slirp4netns utility to configure the host network and simulate network access. ( Refer man slirp4netns for information on various options)
#slirp4netns --configure --mtu=65520 --disable-host-loopback 28354 tap0
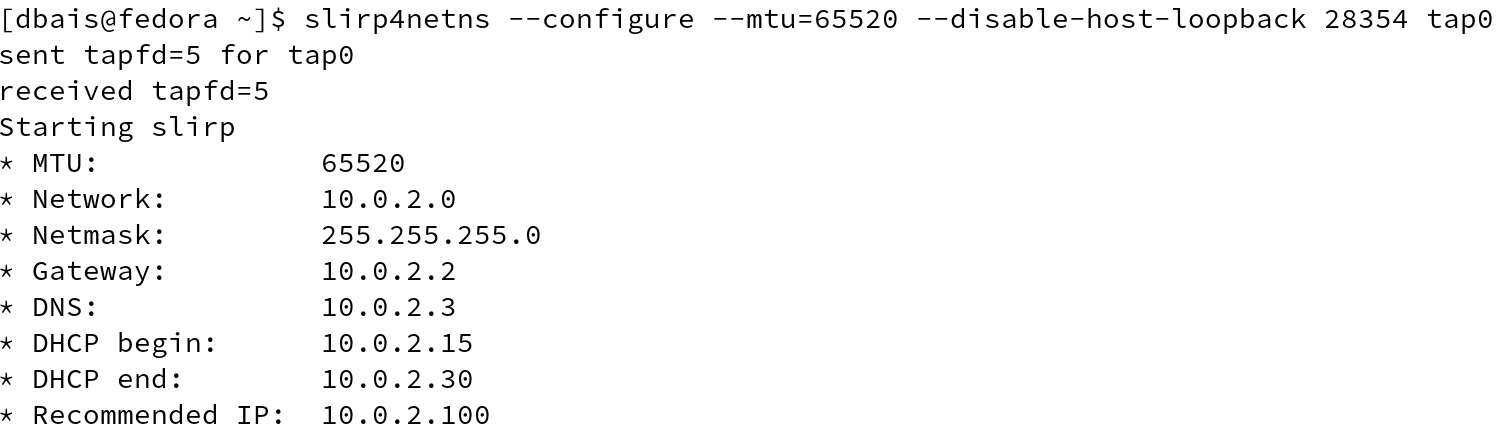
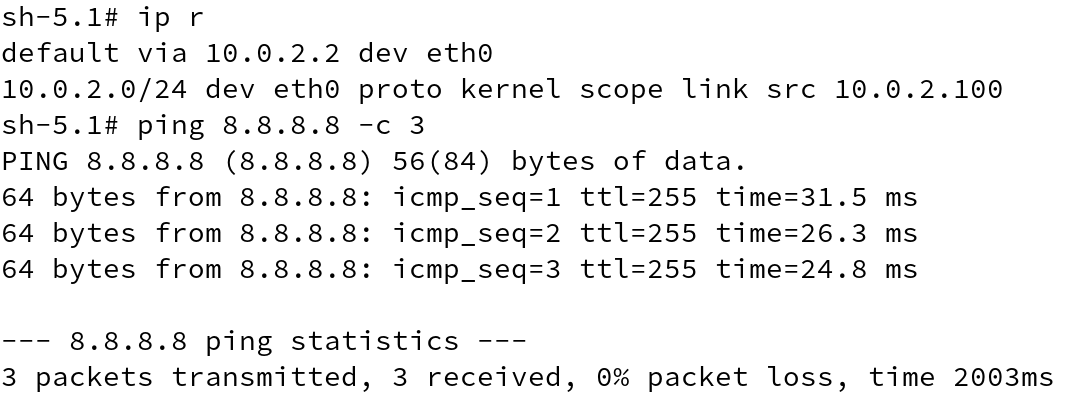
IP address will be set to 10.0.2.100 (network address + 100) by default. Now back to first terminal where, we displayed the list of network interfaces in our namespace, we will be able to see another interface tap0, which has been assigned an IP addess by slirp.
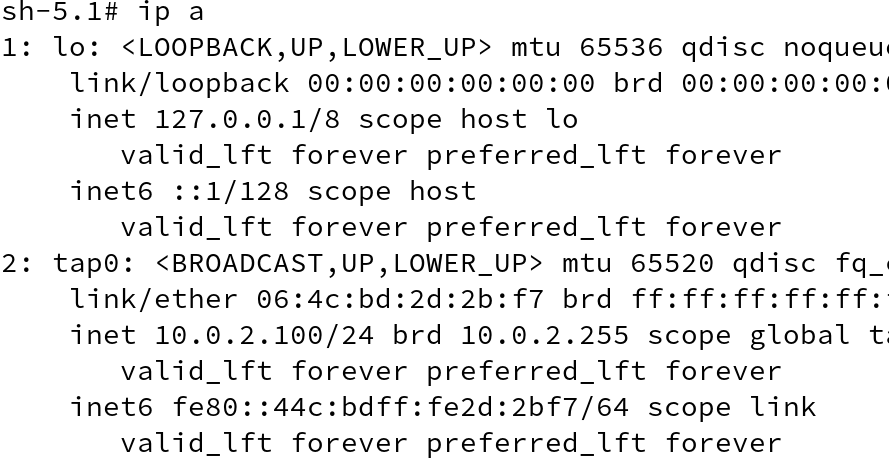
Can I change this interface name to eth0?
Why not, lets try that also. Run command slirp4netns --configure --mtu=65520 --disable-host-loopback 14793 eth0.
Go ahead and observe the change. We can even try to ping to external world and that works for me.
Now that we have seen, how slirp4netns works, lets apply this understanding to running a rootless container on host using Podman.
We start by running a container using Podman. In rootless Podman, we cannot create full, separate networking for containers, because this feature is not allowed for non-root users. In rootless Podman, we use slirp4netns to configure the host network and simulate a network connectivity for the container.
#podman run -d --name rootlesscontainer -p 8080:8080 quay.io/dbais76/fedora-httpd:1.0
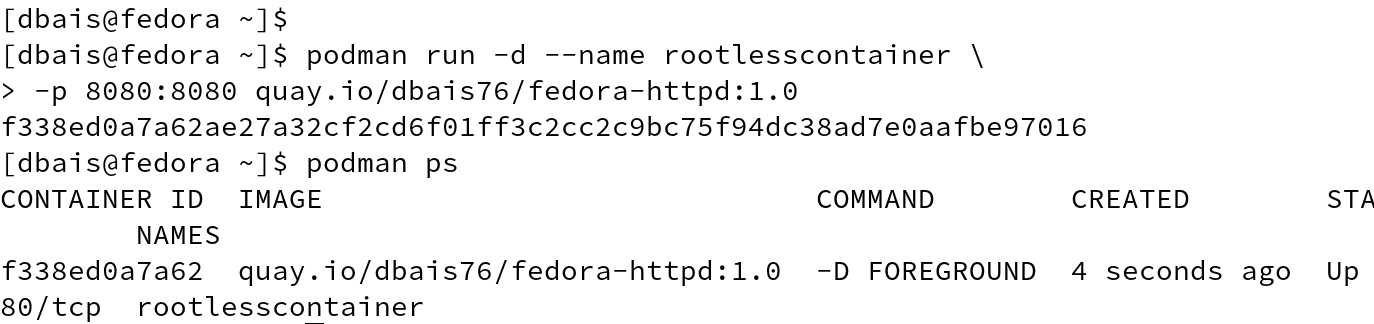
Inspecting the container, we get the PID and using the PID from previous output, execute nsenter to enter network namespaces.

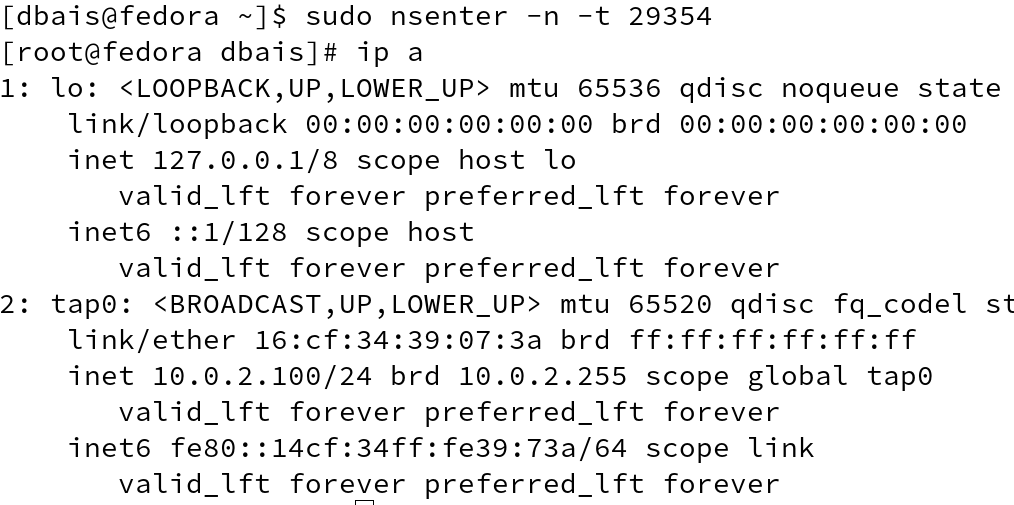
You will be able to see the similar network output and similar behavior when trying to ping any external host.
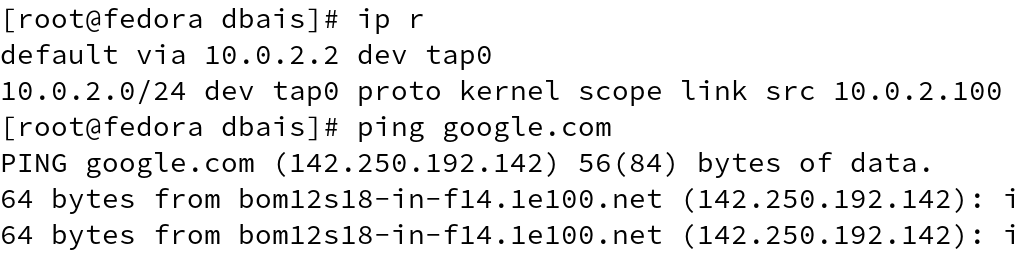
Inspecting the Podman container, we get the network sandbox key, which is also seen in the output of ps -ef command for slirp4netns process.


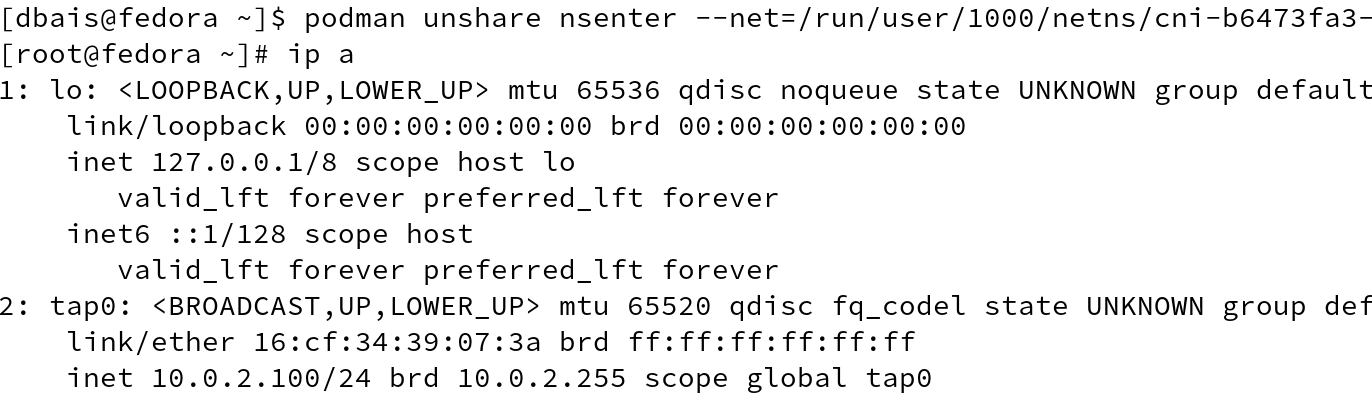
We can also use podman unshare command to connect to the network namespace using the sandbox key and observe, how Slirp helps us to get the network running.
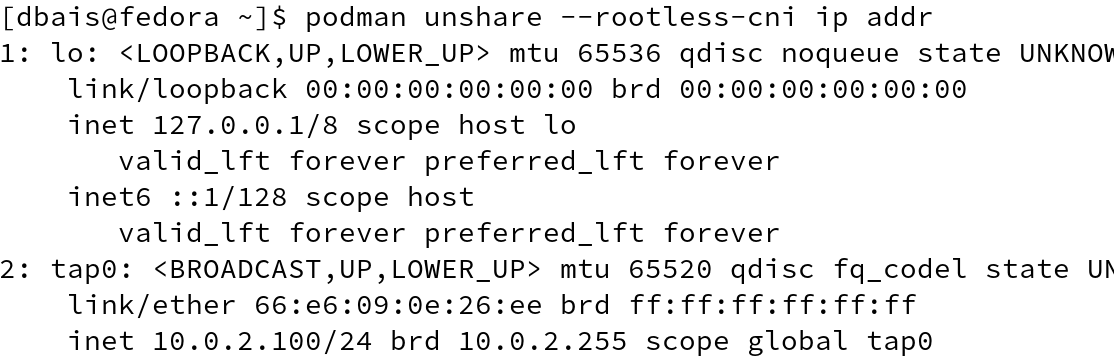
Using --rootless-cni switch for podman unshare command, one can join the rootless network namespace.

In this case, we mapped the host port 8080 to container port 8080. The slirp4netns command creates a tap device that is injected inside the network namespace and network packets are read from slirp4netns which creates the TCP/IP stack in user space. Connections outside network namespace are converted in a socket operations which unprivileged users can execute in host network namespaces.
I hope the information was useful in understanding the rootless networking aspect of Podman.
Happy Reading!!