 Seal the Secret !!
Seal the Secret !!
2022-Aug-18
By:DALEEP SINGH
2022-Jan-17 01:01:15
From Wikipedia - Git is software for tracking changes in any set of files, usually used for coordinating work among programmers collaboratively developing source code during software development. Its goals include speed, data integrity, and support for distributed, non-linear workflows (thousands of parallel branches running on different systems). Git was created by Linus Torvalds in 2005 for the development of the Linux kernel, with other kernel developers contributing to its initial development.
Git is one of the most popular software version control systems used by developers today. developers can write code on local workstations or IDE's and later push/commit them to remote repositories ensuring collaboration between various team members and also allowing developers to pull the source code from remote to local repositories.
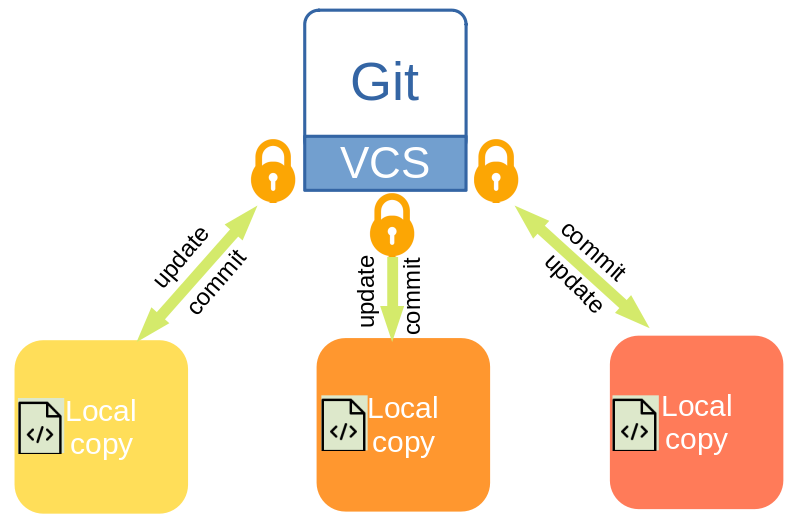
Even though we want to enable and encourage collaboration, we would also want that only trusted members or sources should be able to access the remote repositories to pull or push the source code. Repository visibility can either be Public or Private. Public repository means, anybody could connect and download the source code, which might not be the desired behavior in most of the proprietary source codes. This could also mean that codes are not secure and of this information is exposed and become possibly compromised.
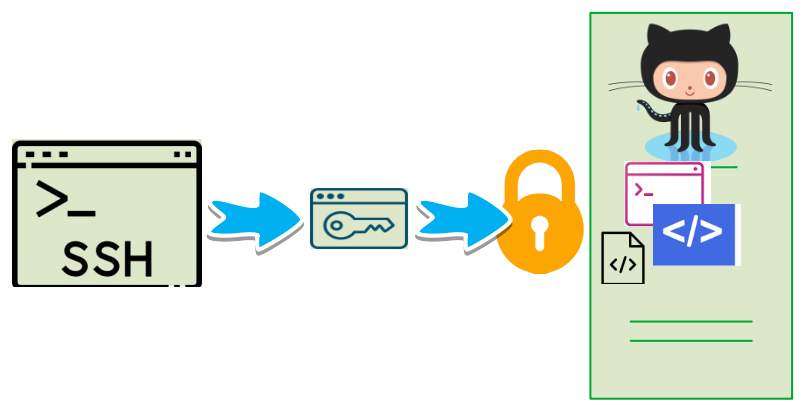
Multiple best practices would be involved to secure the environment and enable trusted access. I am focusing on authenticating to your repository whether for pull or push using SSH. This will encrypt the traffic and also authenticate using the pair of SSH keys. The SSH private key could be and should be protected with a passphrase and also kept secure on the workstation. You can manage SSH keys on your servers using SSH agent forwarding, HTTPS with OAuth tokens, deploy keys, or machine users. I am going to use Deploy Keys in this article.
Deploy Keys are SSH keys that are created to grant access to a single repository and it does not attach the key to the user account making it suitable for defining access selectively. Based on your requirements, deploy keys can also be used to provide Write access on the repository, by default they are read-only. The drawback of Deploy Key is that you can't reuse a deploy key for multiple repositories.
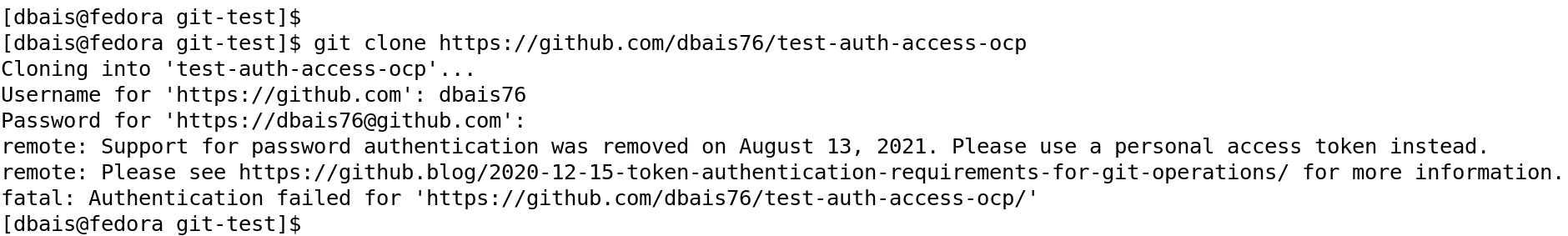
Let me take you through the steps to create and implement Deploy Keys to connect to a private repository. Before implementing the deploy keys, if I try to access the repository now, I get an error message to authenticate as shown in the below snapshot.
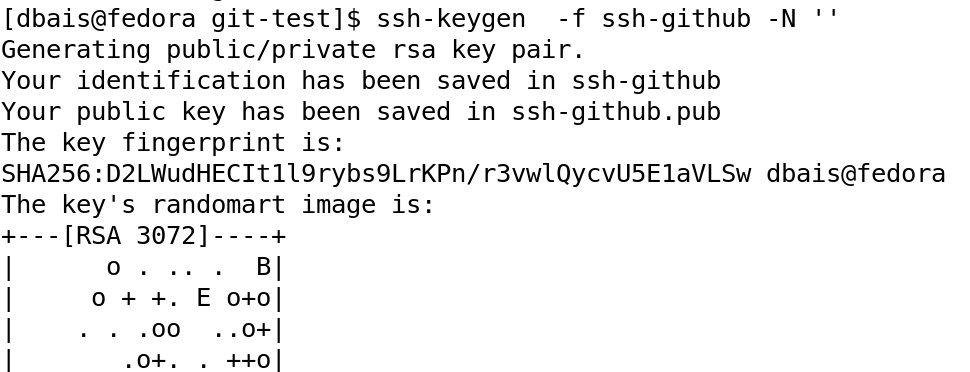
Using ssh-keygen, let us create the SSH keys to be deployed. As you can see, we have a pair of SSH keys, a private and a public key.
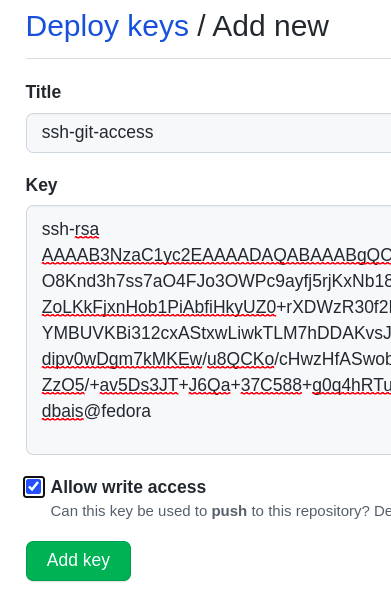
Open a text editor and copy the content of the public key and we need to put that in Deploy Keys in our Git repository. In your Git repository, click Settings, look for Deploy keys from the menu options on the left-hand side and click Deploy Keys. Paste the content of your public key to Deploy Keys and give a name to identify the key. This takes care of the Git for us and now we can move to connect from the local workstation to the repository.
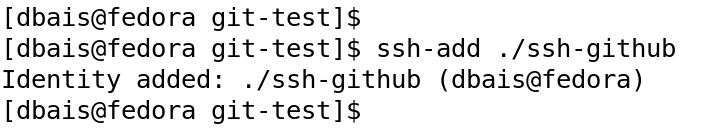
On the workstation, we need to add the key to SSH so that using the private key, we could authenticate to the Git repository. Execute command #ssh-add ./ssh-github to add the key. My SSH key is in the current working directory. You can also use the ssh-agent utility if you have protected the key with a passphrase also and don't want to enter the passphrase every time you operate.
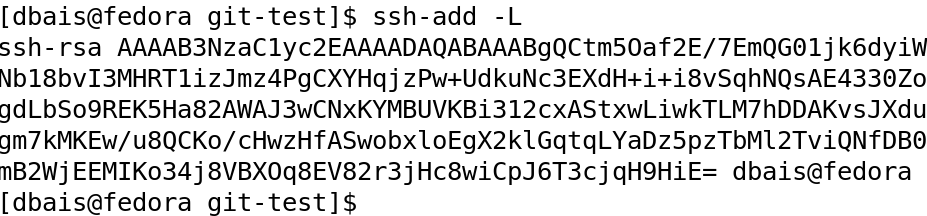
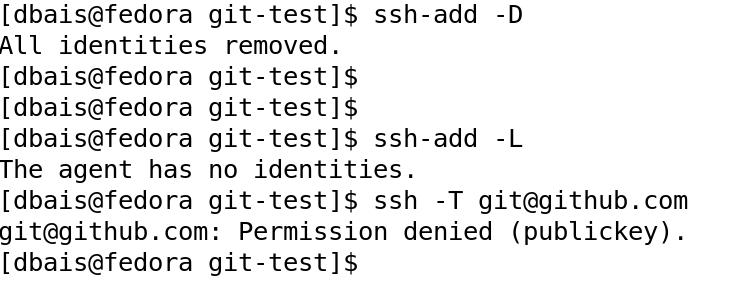
You can also validate the key being added by running the command ssh-add -L to list the keys added and also by performing a test connect to Github using the command: ssh -T git@github.com ( refer man ssh-add for more information on common options).

Once confirmed, we can now proceed to clone our source code from the Git repository and start collaborating.
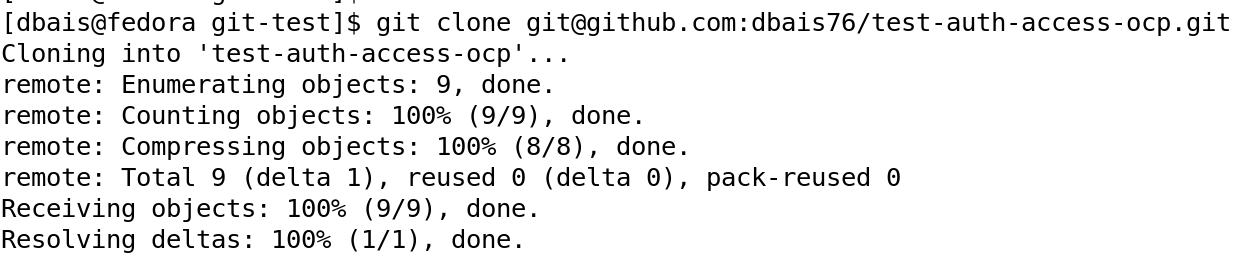
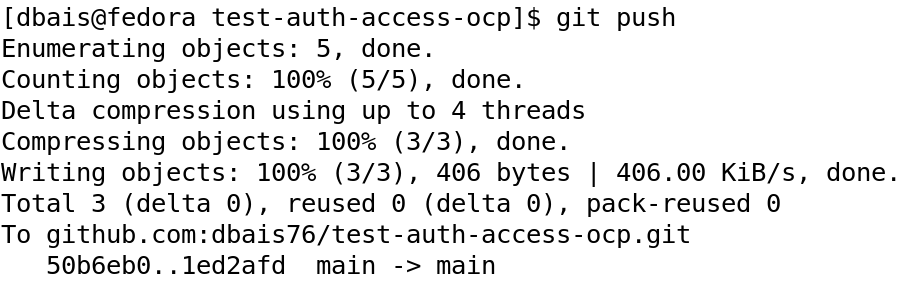
Similarly, we can use the SSH key to push our changes to the remote repository. I made changes to the index.php file and did git add and git command to make changes to the local repository and finally did git push to commit it to remote repository.
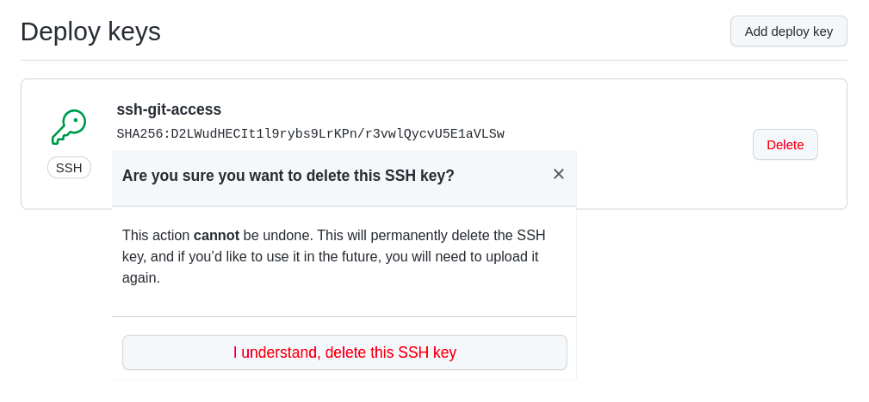
Now that we have seen how to add the keys and use them, we can also do a cleanup, i.e., removing the key from ssh-add and also if needed, delete the key from Github. Run command ssh-add -D to delete the keys from the local workstation and also verify by executing ssh-add -L. From github.com, under Deploy Keys, click Delete against the key you wish to delete and click <I understand, delete this SSH key> button to confirm the action.
I am sure this will help you to connect securely with your git repository.
Happy Reading !!