 Seal the Secret !!
Seal the Secret !!
2022-Aug-18
By:DALEEP SINGH
2022-Jan-16 04:01:47
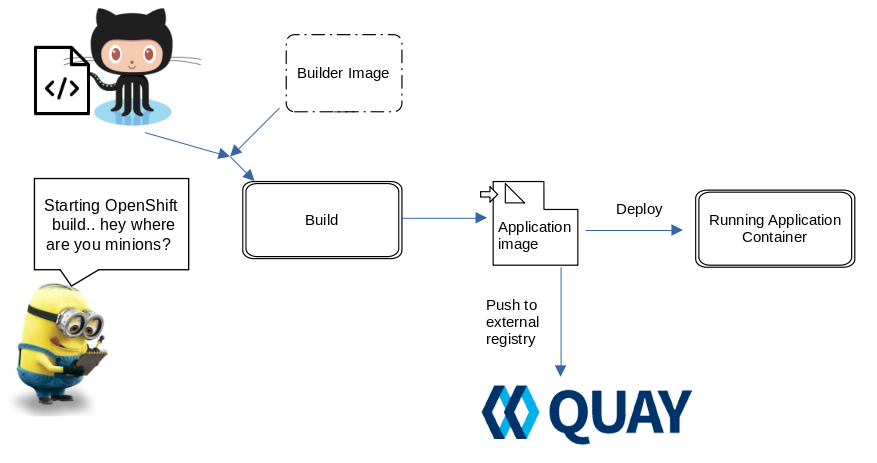
Containers are new normal to deliver and deploy applications and platforms like Kubernetes and OpenShift are the preferred Container orchestration and management platforms. Whereas K8S is adopted by almost all nooks and corner across the industry, OpenShift make it available as the enterprise side of the same with added features like build automation, Routes etc.
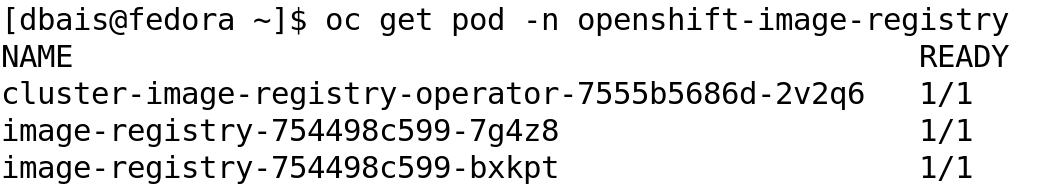
OpenShift also comes along with an inbuilt container registry, which is running as pod in the OpenShift project openshift-image-registry and is used to store the images built result of S2I process or docker build. We can run oc get pod -n openshift-image-registry and oc get service -n openshift-image-registry to check the registry pods and OpenShift service created.

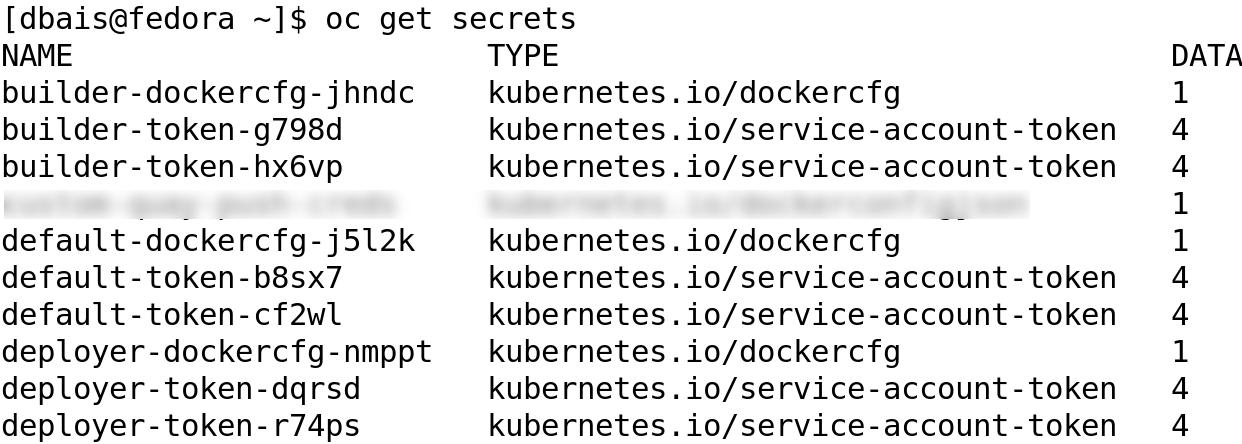
As part of the OpenShift project creation process, it creates three service accounts builder, default and deployer .Along with service account creation, two secrets are automatically added: a) an API token b) Credentials to access OpenShift Container Registry. The generated API token and registry credentials do not expire.

We can inspect any of the dockercfg secret to identify the registry it is pointing to and also credentials associated with it using the command oc get secret --output="jsonpath={.data.\.dockercfg}" | base64 -di which in this case is builder-dockercfg-jhndc.
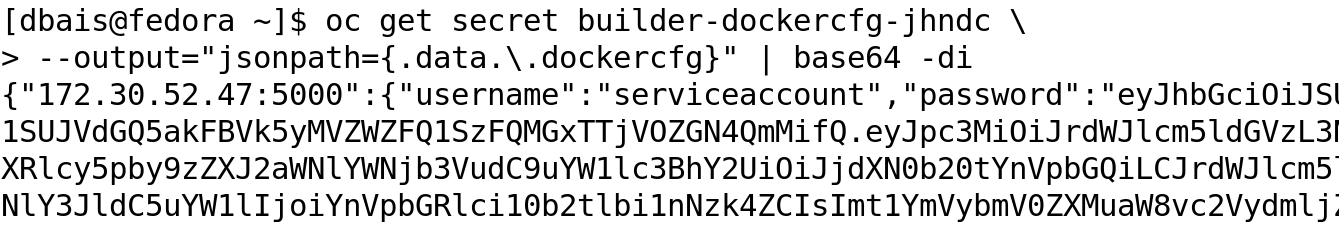
I parsed the output in a JSON editor to show the registry being accessed and it is clearly visible that it is the internal registry which is pointed ( The internal registry service IP and DNS records are being referred).

However, we dont have to necessarily use that internal registry for our applications and it allows us to push our images to external registry and also pull the images from external registry. I am going to demostrate this in two steps:
In both the cases, we will be using OpenShift Secret resource to store the credentials used to push and pull the image from external registry, which is Quay.io in this case. Let first complete part A, which includes getting the credenatials stored as OpenShift Secret and using them in our BuildConfig resource to build the source code into the application and push it to external registry.
The first task would be login to our external registry, Quay.io with username and respective password.
Click Account Settings. Under Docker CLI Password, click "Generate Encrypted Password".

You will be prompted to enter the currect password to authenticate the process.

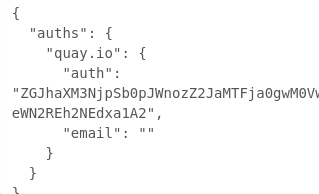
We have several ways to use the credentials now, we are going to select Docker Configuration and click Download -auth.json file. This will be used later to create the OpenShift secret used to store the credentials.

The file consist of account credentials in encrypted form which could be used to pull or push images to Quay registry.
We are presently in our project custom-build and reacy to proceed with next steps on OpenShift.

We will now create an OpenShift Secret resource to store the quay.io credentials. Run the command oc create secret generic custom-quay-push-creds --from-file=.dockerconfigjson=~/Downloads/dbais76-auth.json --type=kubernetes.io/dockerconfigjson to create the secret custom-quay-push-creds.
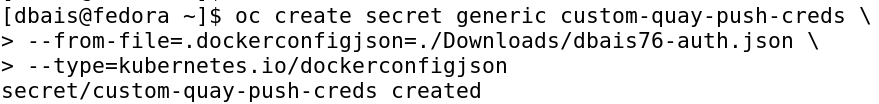
The secret will include the quay credentials in encoded form and you can get more information about the secret by executing oc get -o json secret custom-quay-push-creds | less. I have truncated the output and showing the relevant information only.

With the secret created, we can update our BuildConfig resource with secret under pushSecret and also ensure that .spec.output points to external registry ( as shown in the below image).

We will execute oc create -f custom_build.yaml ( file which holds our BuildConfig resource definition). Start the build process by running oc start-build < build-config.yaml> and confirm that build has successfully started.

Also watch the logs for any build related errors and in the end, to confirm that post build, application image is pushed to external registry. We can also confirm image upload to Quay.io registry and check the Repository and respective tag.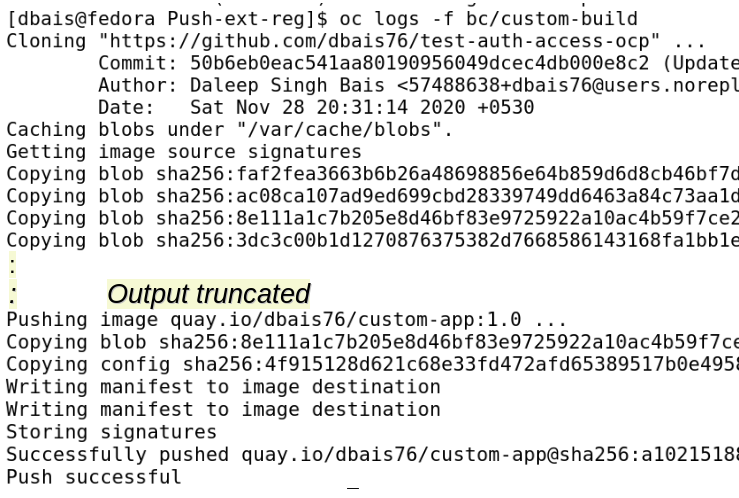
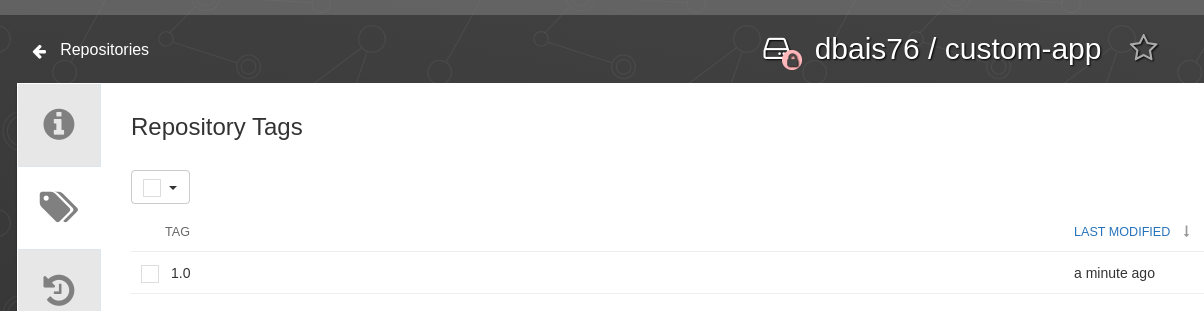
Now to step B, pull the image from authenticated registry and deploy the application.
We would start by creating an ImageStream resource ( what is ImageStream? ) which points to the image on Quay registry. It would use the same secret to download the image metadata and store it in OpenShift datastore. To create the image stream, you can execute command: oc import-image custom-app --from quay.io/dbais76/custom-app:1.0 --confirm
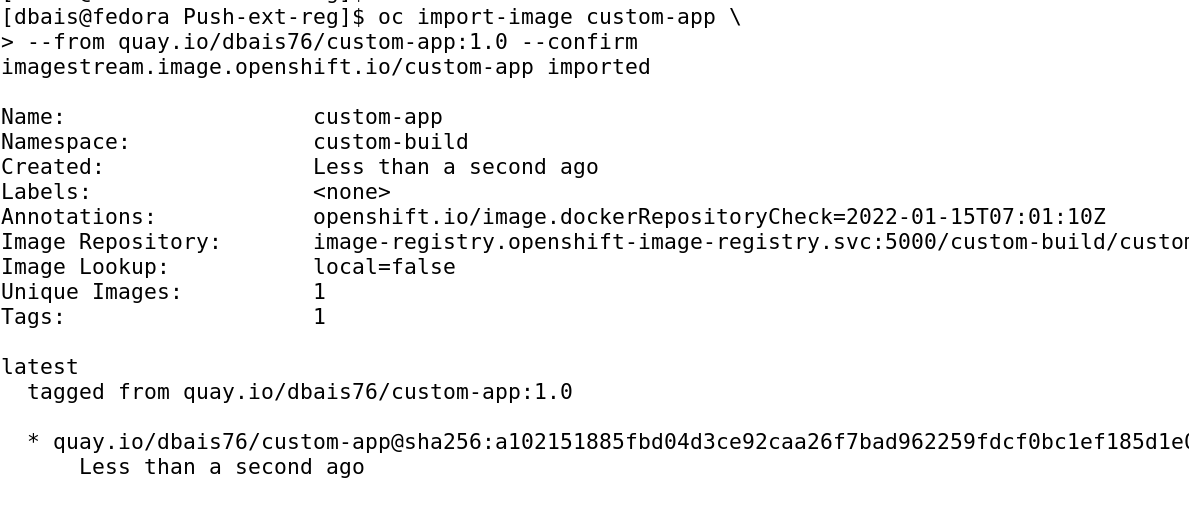

To pull the image while deployment and run the pod, we will bind the secret to ServiceAccount default and assign pull privileges.
#oc secrets link default custom-quay-push-creds --for pull
Once this is done, we ar ready to instruct OpenShift to make the deployment using command: oc new-app --as-deployment-config --name custom-app -i custom-app -l app=customapp

Once application pods are in Running state, we can expose the Service resource to create OpenShift Route which can then be used to access the application.
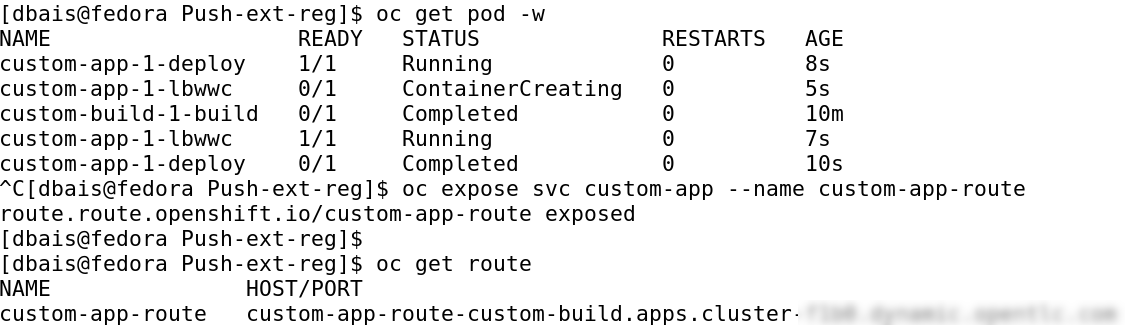
Now we can use this to store our application images created using OpenShift S2I process to external registries and also share them between different environments as part of development cycle.
Happy Reading !!